|
Millions of people all over the world log-on to websites daily, by entering
a username and password, but how secure is this mechanism for entering
websites?
Passwords are easily, forgotten, copied (more often than not, users will
write down their password somewhere), guessed (name of girlfriend, birthday,
street name etc). These are thing that the user has some control over, what
about the hackers? Hacking into a database to copy a list of passwords?
Changing a password in a database?
For
example, on 1st December 2000, a 20-year-old man pleaded guilty
to breaking into two computers owned by NASA's Jet Propulsion Laboratory in
1998 and using one to host Internet chat rooms devoted to hacking. NASA
should surely be one of the most secure systems in the world, but a password
was intercepted, leaked or found, allowing this young man to play inside a
United States Government secure site.
What
if, the only password into a website (or any computer system) was your face,
or a simple object? To log on in the morning a user holds up their object to
their web-cam (which come as standard on most machines now)? That object
could be their calculator, mobile phone, a picture of their signature, a can
of deodorant, a comb, even a strange shape drawn on a piece of paper, as
long as that object was stored in the database the user would be
authenticated.
It is
obvious that more secure methods than this already exist:
But these methods also have problems; both
would require expensive hardware installation on every machine that required
access to the system. Fingerprint and retina scanners are very secure, but
swipe cards are easily lost, stolen or misplaced.
|
Project 1 - 4th Year MEng Project Aims
This will be a Java application, which will
listen for image data being sent to it over a network and then process it as
necessary on the server before sending a response back to the client
applet/application.
- Upon receiving data, load into application.
- Process data.
- Image Analysis.
- Send back response
Project 2 - 3rd Year BEng Project Aims
This should be either an applet or
application on a client machine which has a camera attached.
- Capture Image. (Prompt for object to be moved if in incorrect
position).
- Transmit data to recognition server.
- Receive image data from client on server.
- Possibly forward to administrator for review?
- Transmit response from server to client
- Wait for response from recognition server.
- Display response from recognition server.
The BEng Student should decide any further
details.
These two projects are completely exclusive
to each other,
Project 1 can perform upon it's own as an image analysis/comparison
application.
Project 2 can perform upon it's own as image capture software.
MEng Project Timetable
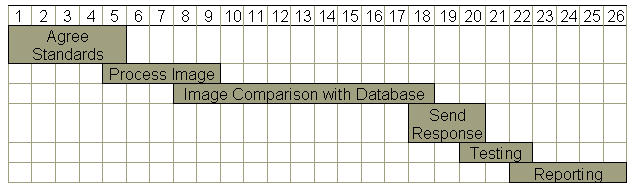
Figure 2.1 – MEng Project Timetable
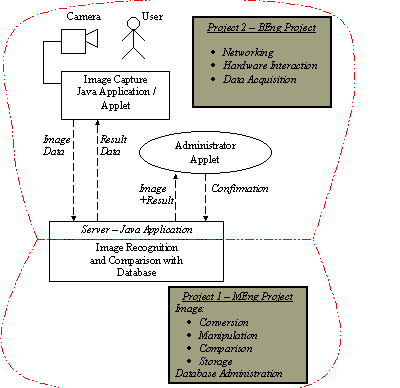
Figure 2.2 -
Division of work between the two projects. |

